Cisco
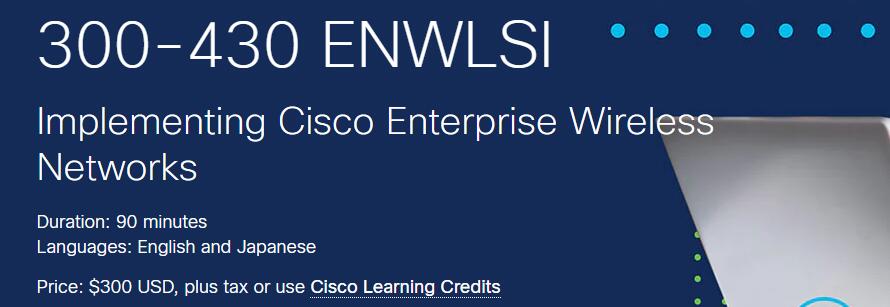
Must be an up-to-date 300-425 pdf dumps to help you pass the Cisco 300-425 ENWLSD exam. We...
Earning the Cisco Certified Specialist – Enterprise Wireless Implementation certificate can significantly advance your career. The new...
In this blog, I’ll walk you through how to use some simple tips to increase your chances...
Passcertguide Offer Everything You Need to Prepare & Pass CCNA 200-301 Exam. Full Attention is the Only...
Passcertguide shares the latest Cisco CCDP 300-101 exam dumps for free exam practice tests and online downloads!...
What do you think of using pass4itsure Cisco 210-260 dumps 100% correct answers? Pass4itsure Cisco 210-260 Dumps...
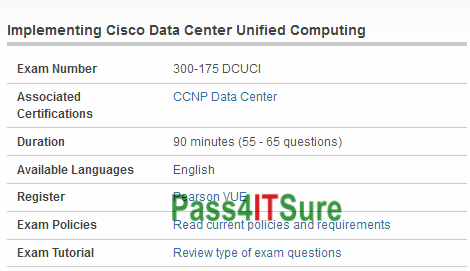
Which version should you buy? Pass4itsure Cisco 300-175 Dumps Practise Questions, Most Popular Cisco 300-175 Dumps PDF Exam...
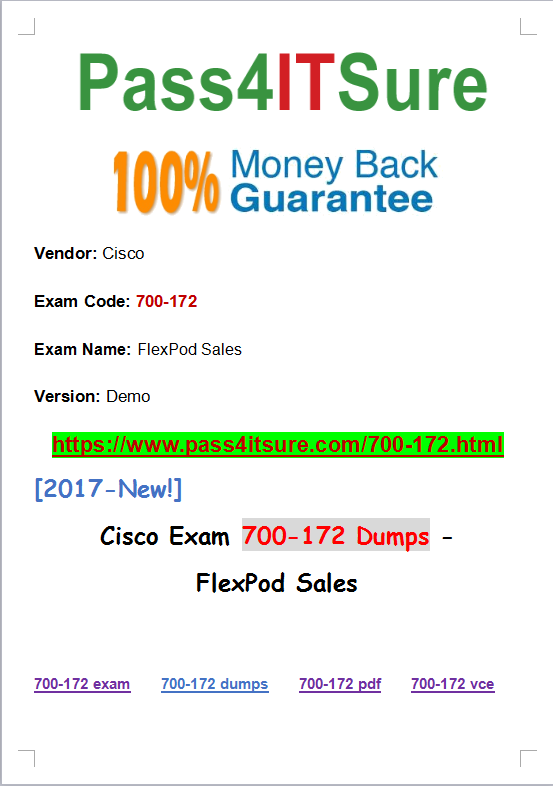
Now are you in preparation for Cisco 700-172 dumps training materials? The FlexPod Sales (700-172) exam is...
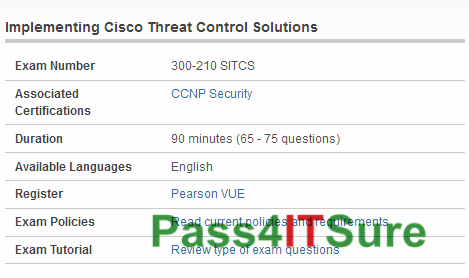
Has anybody attempted the Cisco 300-210 exam? The Implementing Cisco Threat Control Solutions (SITCS) (300-210 SITCS) exam is...