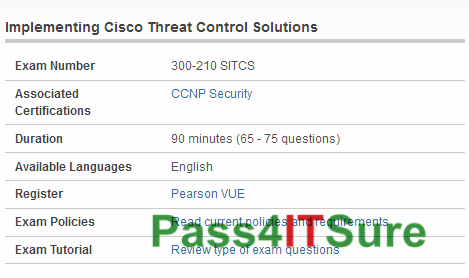
Has anybody attempted the Cisco 300-210 exam? The Implementing Cisco Threat Control Solutions (SITCS) (300-210 SITCS) exam is a 90 minutes (65 – 75 questions) assessment in pass4itsure that is associated with the CCNP Security certification. Most important Cisco 300-210 dumps SITCS exam actual test Youtube study guide is your best choice. “Implementing Cisco Threat Control Solutions (SITCS)” is the exam name of Pass4itsure Cisco 300-210 dumps test which designed to help candidates prepare for and pass the Cisco 300-210 exam. Cisco https://www.pass4itsure.com/300-210.html dumps powerful exam dumps is experiences and results summarized by IT experts in the past years, standing upon the shoulder of predecessors, it will let you further access to success.
[New Cisco 300-210 Dumps Release From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWc2tWemlPb3Vmazg
[New Cisco 600-509 Dumps Release From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWeW42OTIyc3NXNm8
Pass4itsure Cisco 300-210 Dumps Training Program Online Here:
QUESTION 7
What is needed to perform a non-disruptive migration of virtual machines (VMs) between hypervisors?
A. Hypervisors must have access to the same storage volume
B. Physical machines running hypervisors must have the same configuration
C. Hypervisors must be running within the same physical machine
D. Both hypervisors must have the same IP address
300-210 exam Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
VM Migration: Hypervisor-to-Hypervisor
In hypervisor-to-hypervisor VM migration, the entire active state of a VM is moved from one hypervisor to another. This method involves copying the contents of virtual machine memory from the source hypervisor to the target and then transferring the control of the VM’s disk files to the target hypervisor. Because the virtual disks of the VMs are not migrated, this technique requires both source and target hypervisor access to the same storage.
EMC E10-001 Student Resource Guide. Module 12: Remote Replication
QUESTION 8
Which iSCSI name requires an organization to own a registered domain name?
A. IQN
B. EUI
C. WWNN
D. WWPN
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
iSCSI Name
A unique worldwide iSCSI identifier, known as an iSCSI name, is used to identify the initiators and targets within an iSCSI network to facilitate communication. The unique identifier can be a combination of the names of the department, application, or manufacturer, serial number, asset number, or any tag that can be used to recognize and manage the devices. Following are two types of iSCSI names commonly used:· iSCSI Qualified Name (IQN): An organization must own a registered domain name to generate iSCSI Qualified Names. This domain name does not need to be active or resolve to an address. It just needs to be reserved to prevent other organizations from using the same domain name to generate iSCSI names. A date is included in the name to avoid potential conflicts caused by the transfer of domain names. An example of an IQN is iqn.2008-02.com.example:optional_string. The optional_string provides a serial number, an asset number, or any other device identifiers. An iSCSI Qualified Name enables storage administrators to assign meaningful names to iSCSI devices, and therefore, manage those devices more easily. Extended Unique Identifier (EUI): An EUI is a globally unique identifier based on the IEEE EUI-64 naming standard. An EUI is composed of the eui prefix followed by a 16-character exadecimal name, such as
eui.0300732A32598D26. In either format, the allowed special characters are dots, dashes, and blank spaces. EMC E10-001 Student Resource Guide. Module 6: IP SAN and FCoE
QUESTION 9
Which data center requirement refers to applying mechanisms that ensure data is stored and retrieved as it was received?
A. Integrity
B. Availability
C. Security
D. Performance
300-210 dumps Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
Information Security Framework
The basic information security framework is built to achieve four security goals, confidentiality, integrity, and availability (CIA) along with accountability. This framework incorporates all security standards, procedures and controls, required to mitigate threats in the storage infrastructure environment. Confidentiality: Provides the required secrecy of information and ensures that only authorized users have access to data. This requires authentication of users who need to access information. Data in transit (data transmitted over cables) and data at rest (data residing on a primary storage, backup media, or in the archives) can be encrypted to maintain its confidentiality. In addition to restricting unauthorized users from accessing information, confidentiality also requires to implement traffic flow protection measures as part of the security protocol. These protection measures generally include hiding source and destination addresses, frequency of data being sent, and amount of data sent. Integrity: Ensures that the information is unaltered . Ensuring integrity requires detection and protection against unauthorized alteration or deletion of information. Ensuring integrity stipulate measures such as error detection and correction for both data and systems. Availability: This ensures that authorized users have reliable and timely access to systems, data and applications residing on these systems. Availability requires protection against unauthorized deletion of data and denial of service. Availability also implies that sufficient resources are available to provide a service. Accountability: Refers to accounting for all the events and operations that take place in the data center
infrastructure. The accountability service maintains a log of events that can be audited or traced later for the purpose of security.
QUESTION 10
What describes a landing zone in a disk drive?
A. Area on which the read/write head rests
B. Area where the read/write head lands to access data
C. Area where the data is buffered before writing to platters
D. Area where sector-specific information is stored on the disk
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
Disk Drive Components
The key components of a hard disk drive are platter, spindle, read-write head, actuator arm assembly, and controller board. I/O operations in a HDD is performed by rapidly moving the arm across the rotating flat platters coated with magnetic particles. Data is transferred between the disk controller and magnetic platters through the read-write (R/W) head which is attached to the arm. Data can be recorded and erased on magnetic platters any number of times. Platter: A typical HDD consists of one or more flat circular disks called platters. The data is recorded on these platters in binary codes (0s and 1s). The set of rotating platters is sealed in a case, called Head Disk Assembly (HDA). A platter is a rigid, round disk coated with magnetic material on both surfaces (top and bottom). The data is encoded by polarizing the magnetic area, or domains, of the disk surface. Data can be written to or read from both surfaces of the platter. The number of platters and the storage capacity of each platter determine the total capacity of the drive. Spindle: A spindle connects all the platters and is connected to a motor. The motor of the spindle rotates with a constant speed. The disk platter spins at a speed of several thousands of revolutions per minute (rpm). Common spindle speeds are 5,400 rpm, 7,200 rpm, 10,000 rpm, and 15,000 rpm. The speed of the platter is increasing with improvements in technology; although, the extent to which it can be improved is limited. Read/Write Head: Read/Write (R/W) heads, read and write data from or to platters. Drives have two R/W heads per platter, one for each surface of the platter. The R/W head changes the agnetic polarization on the surface of the platter when writing data. While reading data, the head detects the magnetic polarization on the surface of the platter. During reads and writes, the R/W head senses the magnetic polarization and never touches the surface of the platter. When the spindle is rotating, there is a microscopic air gap maintained between the R/W heads and the platters, known as the head flying height. This air gap is removed when the spindle stops rotating and the R/W head rests on a special area on the platter near the spindle. This area is called the landing zone . The landing zone is coated with a lubricant to reduce friction between the head and the platter. The logic on the disk drive ensures that heads are moved to the landing zone before they touch the surface. If the drive malfunctions and the R/W head accidentally touches the surface of the platter outside the landing zone, a head crash occurs. In a head crash, the magnetic coating on the platter is scratched and may cause damage to the R/W head. A head crash generally results in data loss. Actuator Arm Assembly: R/W heads are mounted on the actuator arm assembly, which positions the R/W head at the location on the platter where the data needs to be written or read. The R/W heads for all platters on a drive are attached to one actuator arm assembly and move across the platters simultaneously. Drive Controller Board: The controller is a printed circuit board, mounted at the bottom of a disk drive. It consists of a microprocessor, internal memory, circuitry, and firmware. The firmware controls the power to the spindle motor and the speed of the motor. It also manages the communication between the drive and the host. In addition, it controls the R/W operations by moving the actuator arm and switching between different R/W heads, and performs the optimization of data access.
QUESTION 11
What is a characteristic of unified storage?
A. Supports multiple protocols for data access and managed through a single management interface
B. Supports a common protocol for data access and managed through a unified management interface
C. Provides compute, storage, and network virtualization products in one solution
D. Stores all data in the form of objects and managed through a unified management interface
300-210 pdf Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 12
What defines the time taken to position the read/write head across the platter with a radial movement in a
disk drive?
A. Seek time
B. Rotational latency
C. Data transfer time
D. Service time
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
Seek Time
The seek time (also called access time) describes the time taken to position the R/W heads across the platter with a radial movement (moving along the radius of the platter). In other words, it is the time taken to position and settle the arm and the head over the correct track. Therefore, the lower the seek time, the faster the I/O operation. Disk vendors publish the following seek time specifications: Full Stroke: The time taken by the R/W head to move across the entire width of the disk, from the innermost track to the outermost track. Average: The average time taken by the R/W head to move from one random track to another, normally listed as the time for one-third of a full stroke. Track-to-Track: The time taken by the R/W head to move between adjacent tracks.
Each of these specifications is measured in milliseconds. The seek time of a disk is typically specified by the drive manufacturer. The average seek time on a modern disk is typically in the range of 3 to 15 milliseconds. Seek time has more impact on the I/O operation of random tracks rather than the adjacent
tracks. To minimize the seek time, data can be written to only a subset of the available cylinders. This results in lower usable capacity than the actual capacity of the drive. For example, a 500-GB disk drive is set up to use only the first 40 percent of the cylinders and is effectively treated as a 200-GB drive. This is known as short stroking the drive.
This time you should be thought of Cisco 300-210 dumps website that is good helper of your exam. “Troubleshooting Cisco Data Center Infrastructure”, also known as 300-210 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 300-210 dumps exam questions answers are updated (330 Q&As) are verified by experts. The associated certifications of 300-210 dumps is CCNP Security. With the development of society, IT industry has been tremendously popular. And more and more people join IT certification exam and want to get https://www.pass4itsure.com/300-210.html dumps IT certificate that make them go further in their career.





