Security+ focuses on the latest trends and techniques in risk management, risk mitigation, threat management and intrusion detection.We share the latest effective CompTIA CySA+ CS0-001 exam dumps online Practice test to improve your skills! You can also choose CS0-001 PDF! Get the full CS0-001 dumps: https://www.pass4itsure.com/cs0-001.html (Q&As: 241 ) to pass the exam easily!
The CompTIA Cybersecurity Analyst (CySA+) certification verifies that successful candidates have the knowledge and skills required to configure and use threat detection tools, perform data analysis and interpret the results to identify vulnerabilities, threats and risks to an organization, with the end goal of securing and protecting applications and systems within an organization.
[PDF] Free CompTIA CySA+ CS0-001 pdf dumps download from Google Drive: https://drive.google.com/open?id=1XIeMmZlYQKrMC4ZoSuPmSWZ_TO5OaOfs
[PDF] Free Full CompTIA pdf dumps download from Google Drive: https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
CompTIA (CySA+) Cybersecurity Analyst+ Certification | CompTIA IT Certifications: https://certification.comptia.org/certifications/cybersecurity-analyst
Latest effective CompTIA CySA+ CS0-001 Exam Practice Tests
QUESTION 1
A security analyst begins to notice the CPU utilization from a sinkhole has begun to spike Which of the following
describes what may be occurring?
A. Someone has logged on to the sinkhole and is using the device
B. The sinkhole has begun blocking suspect or malicious traffic
C. The sinkhole has begun rerouting unauthorized traffic
D. Something is controlling the sinkhole and causing CPU spikes due to malicious utilization.
Correct Answer: B
QUESTION 2
Following a recent security breach, a post-mortem was done to analyze the driving factors behind the breach. The
cybersecurity analysis discussed potential impacts, mitigations, and remediations based on current events and
emerging threat vectors tailored to specific stakeholders. Which of the following is this considered to be?
A. Threat intelligence
B. Threat information
C. Threat data
D. Advanced persistent threats
Correct Answer: A
QUESTION 3
During a routine network scan, a security administrator discovered an unidentified service running on a new embedded
and unmanaged HVAC controller, which is used to monitor the company\\’s datacenter:
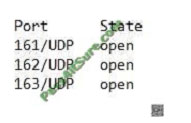
The enterprise monitoring service requires SNMP and SNMPTRAP connectivity to operate. Which of the following
should the security administrator implement to harden the system?
A. Patch and restart the unknown service.
B. Segment and firewall the controller\\’s network.
C. Disable the unidentified service on the controller.
D. Implement SNMPv3 to secure communication.
E. Disable TCP/UDP ports 161 through 163.
Correct Answer: A
QUESTION 4
A recently issued audit report highlight exception related to end-user handling of sensitive data access and credentials.
A security manager is addressing the findings. Which of the following activities should be implemented?
A. Update the password policy
B. Increase training requirements
C. Deploy a single sign-on platform
D. Deploy Group Policy Objects
Correct Answer: C
QUESTION 5
Which of the following is a control that allows a mobile application to access and manipulate information which should
only be available by another application on the same mobile device (e.g. a music application posting the name of the
current song playing on the device on a social media site)?
A. Co-hosted application
B. Transitive trust
C. Mutually exclusive access
D. Dual authentication
Correct Answer: B
QUESTION 6
Following a data compromise, a cybersecurity analyst noticed the following executed query:
SELECT * from Users WHERE name = rick OR 1=1
Which of the following attacks occurred, and which of the following technical security controls would BEST reduce the
risk of future impact from this attack? (Select TWO).
A. Cookie encryption
B. XSS attack
C. Parameter validation
D. Character blacklist
E. Malicious code execution
F. SQL injection
Correct Answer: CF
https://lwn.net/Articles/177037/
QUESTION 7
A nuclear facility manager (determined the need to monitor utilization of water within the facility. A startup company just
announced a state-of-the-art solution to address the need for integrality \\’be business and ICS networks The solution
leqmies a very small agent lo be installed on the 1CS equipment Which of the following is the MOST important security
control for the manager to invest in to protect the facility?
A. Run a penetration lest on the installed agent.
B. Require that the solution provider make the agent source code available for analysis.
C. Require thorough guides for administrator and users
D. Install the agent tor a week on a test system and monitor the activities
Correct Answer: A
QUESTION 8
Which of the following BEST describes the offensive participants in a tabletop exercise?
A. Red team
B. Blue team
C. System administrators
D. Security analysts
E. Operations team
Correct Answer: A
QUESTION 9
File integrity monitoring states the following files have been changed without a written request or approved change. The
following change has been made:
chmod 777 -Rv /usr
Which of the following may be occurring?
A. The ownership pf /usr has been changed to the current user.
B. Administrative functions have been locked from users.
C. Administrative commands have been made world readable/writable.
D. The ownership of/usr has been changed to the root user.
Correct Answer: C
QUESTION 10
An analyst was testing the latest version of an internally developed CRM system. The analyst created a basic user
account. Using a few tools in Kali\\’s latest distribution, the analyst was able to access configuration files, change
permissions on folders and groups, and delete and create new system objects. Which of the following techniques did
the analyst use to perform these unauthorized activities?
A. Impersonation
B. Privilege escalation
C. Directory traversal
D. Input injection
Correct Answer: C
QUESTION 11
A retail corporation with widely distributed store locations and IP space must meet PCI requirements relating to
vulnerability scanning. The organization plans to outsource this function to a third party to reduce costs.
Which of the following should be used to communicate expectations related to the execution of scans?
A. Vulnerability assessment report
B. Lessons learned documentation
C. SLA
D. MOU
Correct Answer: C
QUESTION 12
A cybersecurity analyst has received an alert that well-known “call home” messages are continuously observed by
network sensors at the network boundary. The proxy firewall successfully drops the messages. After determining the
alert was a true positive, which of the following represents the MOST likely cause?
A. Attackers are running reconnaissance on company resources.
B. An outside command and control system is attempting to reach an infected system.
C. An insider is trying to exfiltrate information to a remote network.
D. Malware is running on a company system.
Correct Answer: B
QUESTION 13
A cybersecurity analyst is completing an organization\\’s vulnerability report and wants it to reflect assets accurately.
Which of the following items should be in the report?
A. Processor utilization
B. Virtual hosts
C. Organizational governance
D. Log disposition
E. Asset isolation
Correct Answer: B
As attackers have learned to evade traditional signature-based solutions, such as firewalls, an analytics-based approach within theIT security industry is increasingly important for most organizations. The behavioral analytics skills covered by CySA+ identify and combat malware, and advanced persistent threats (APTs), resulting in enhanced threat visibility across a broad attack surface.
Share 13 of the latest CompTIA CySA+ CS0-001 dumps Practice tests for free to help you improve your skills. CS0-001 PDF download Online! Get the full CS0-001 dumps: https://www.pass4itsure.com/cs0-001.html (Q&As: 241 ). Easily pass the exam!
[PDF] Free CompTIA CySA+ CS0-001 pdf dumps download from Google Drive: https://drive.google.com/open?id=1XIeMmZlYQKrMC4ZoSuPmSWZ_TO5OaOfs
[PDF] Free Full CompTIA pdf dumps download from Google Drive: https://drive.google.com/open?id=1SnVb1WLCtG5umIgtJ4zeNNSpuAFWZ3yg
pass4itsure Promo Code 12% Off
related: https://www.passcertguide.com/100-pass-rate-cisco-700-172-dumps-flexpod-sales-exam/


