I guess you need to update the CAS-004 dumps. Welcome here to get it. If you are determined to pass the CompTIA CASP+ CAS-004 exam for the first time, CAS-004 dumps will be your preparation for the CompTIA Advanced Security Practitioner (CASP+) certification the right CAS-004 preparation guide.
Pass4itSure CAS-004 dumps https://www.pass4itsure.com/cas-004.html updated dumps consist of real CAS-004 practice test questions and answers that will make you truly ready for the CAS-004 exam.
CompTIA CASP+ CAS-004 exam, How much do you know?
Learn the fundamentals of CAS-004 –

Exam Number: CAS-004
Number of questions: up to 90
Question Type: Multiple Choice and Performance-Based
Exam Duration: 165 minutes
Recommended Experience • At least ten years of general IT practical experience, of which at least five years are broad
Examination content:
1.0 Security Architecture 29%
2.0 Security Operations 30%
3.0 Security Engineering and Cryptography 26%
4.0 Governance, Risk, and Compliance 15%
Certification: CompTIA Advanced Security Practitioner CASP+
Where can I find the correct CompTIA CASP+ CAS-004 preparation guide?
The right preparation guide is key to passing the CompTIA Advanced Security Practitioner (CASP+) certification exam. The Pass4itSure CAS-004 dumps are your first choice.
Pass4itSure, as the provider of CAS-004 dumps, has many years of experience in exam preparation and is trustworthy. It is highly recommended that you use the CAS-004 dumps to prepare for the exam.
Share some CAS-004 free dumps exam practice:
QUESTION 1
A developer implements the following code snippet.

Which of the following vulnerabilities does the code snippet resolve?
A. SQL inject
B. Buffer overflow
C. Missing session limit
D. Information leakage
Correct Answer: D
QUESTION 2
Ransomware encrypted the entire human resources files for a large financial institution. Security operations
personnel were unaware of the activity until it was too late to stop it. The restoration will take approximately four hours,
and the last backup occurred 48 hours ago.
The management team has indicated that the RPO for a disaster recovery event for this data classification is 24 hours. Based on RPO requirements, which of the following recommendations should the management team make?
A. Leave the current backup schedule intact and pay the ransom to decrypt the data.
B. Leave the current backup schedule intact and make the human resources files read-only.
C. Increase the frequency of backups and create SIEM alerts for IOCs.
D. Decrease the frequency of backups and pay the ransom to decrypt the data.
Correct Answer: C
QUESTION 3
After a security incident, a network security engineer discovers that a portion of the company\\’s sensitive external traffic has been redirected through a secondary ISP that is not normally used. Which of the following would BEST secure the routes while allowing the network to function in the event of a single provider failure?
A. Disable BGP and implement a single static route for each internal network.
B. Implement a BGP route reflector.
C. Implement an inbound BGP prefix list.
D. Disable BGP and implement OSPF.
Correct Answer: B
QUESTION 4
A security analyst is comparing two virtual servers that were bum from the same image and patched at the same regular intervals Server A is used to host a public-facing website, and Server B runs accounting software inside the firewalled accounting network. The analyst runs the same command and obtains the following output from Server A and Server B. respectively:
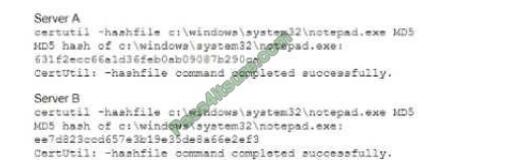
Which of the following will the analyst most likely use NEXT?
A. Exploitation tools
B. Hash cracking tools
C. Malware analysis tools
D. Log analysis tools
Correct Answer: A
QUESTION 5
During a system penetration test, a security engineer successfully gained access to a shell on a Linux host as a
standard user and wants to elevate the privilege levels. Which of the following is a valid Linux post-exploitation method
to use to accomplish this goal?
A. Spawn a shell using sudo and an escape string such as sudo vim -c ‘!sh’.
B. Perform ASIC password cracking on the host.
C. Read the /etc/passwd file to extract the usernames.
D. Initiate unquoted service path exploits.
E. Use the UNION operator to extract the database schema.
Correct Answer: C
Reference: https://docs.rapid7.com/insightvm/elevating-permissions/
QUESTION 6
A facilities manager requests approval to deploy a new key management system that integrates with logical network
access controls to provide conditional access. The security analyst who is assessing the risk has no experience with the
category of products. Which of the following is the FIRST step the analyst should take to begin the research?
A. Seek documented industry best practices.
B. Review the preferred vendor\\’s white papers.
C. Compare the product function to relevant RFCs
D. Execute a non-disclosure agreement with the vendor
Correct Answer: A
QUESTION 7
A networking team was asked to provide secure remote access to all company employees. The team decided to use
a client-to-site VPN as a solution. During a discussion, the Chief Information Security Officer raised a security concern
and asked the networking team to route the Internet traffic of remote users through the main office infrastructure. Doing this would prevent remote users from accessing the Internet through their local networks while connected to the VPN.
Which of the following solutions does this describe?
A. Full tunneling
B. Asymmetric routing
C. SSH tunneling
D. Split tunneling
Correct Answer: B
QUESTION 8
Given the following log snippet from a web server:
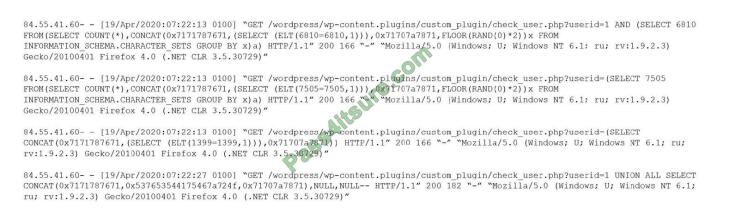
Which of the following BEST describes this type of attack?
A. SQL injection
B. Cross-site scripting
C. Brute-force
D. Cross-site request forgery
Correct Answer: D
QUESTION # 9
A company is outsourcing to an MSSP that performs managed detection and response services. The MSSP requires a
server to be placed inside the network as a log aggregate and allows remote access to the MSSP analyst. Critical devices send logs to the log aggregator, where data is stored for 12 months locally before being archived in a multitenant cloud.
The data is then sent from the log aggregate to a public IP address in the MSSP data center for analysis.
A security engineer is concerned about the security of the solution and notes the following:
1. The critical device sends cleartext logs to the aggregator.
2. The log aggregator utilizes full disk encryption.
3. The log aggregator sends to the analysis server via port 80.
4. MSSP analysis utilizes an SSL VPN with MFA to access the log aggregator remotely.
5. The data is compressed and encrypted prior to being achieved in the cloud.
Which of the following should be the engineer\’s GREATEST concern?
A. Hardware vulnerabilities introduced by the log aggregate server
B. Network bridging from a remote access VPN
C. Encryption of data in transit
D. Multinancy and data remnants in the cloud
Correct Answer: C
QUESTION 10
A disaster recovery team learned of several mistakes that were made during the last disaster recovery parallel test.
Computational resources ran out at 70% of the restoration of critical services. Which of the following should be modified to prevent the issue from reoccurring?
A. Recovery point objective
B. Recovery time objective
C. Mission-essential functions
D. Recovery service level
Correct Answer: B
Reference: https://www.nakivo.com/blog/disaster-recovery-in-cloud-computing/
QUESTION 11
SIMULATION
You are a security analyst tasked with interpreting a Nmap scan output from Company A\’s privileged network.
The company\’s hardening guidelines indicate the following:
1. There should be one primary server or service per device.
2. Only default ports should be used.
3. Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found, add a device entry to the Devices Discovered list, with the following information:
1. The IP address of the device
2. The primary server or service of the device
3. The protocol(s) that should be disabled based on the hardening guidelines
To select multiple protocols, use CTRL+CLICK.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
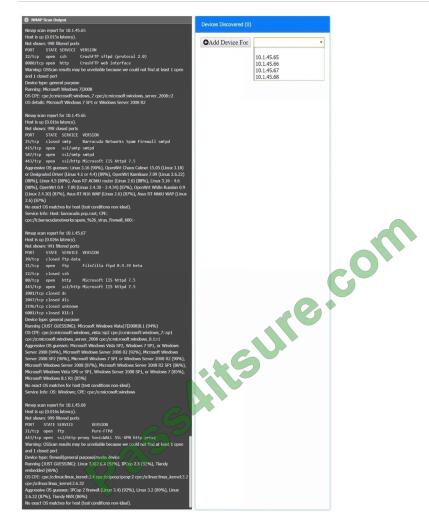
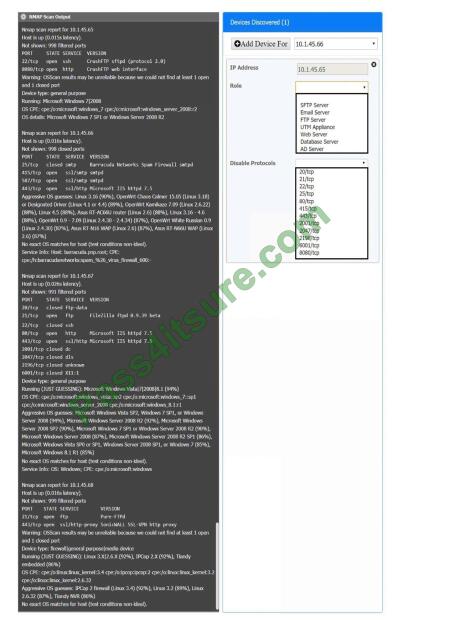
Correct Answer: Check the answer in the explanation.
10.1.45.65 -FTP Server -Disable 8080
10.1.45.66 -Email Serve -Disable 25 and 415
10.1.45.67 -Web Server -Disable 21, 80
10.1.45.68 -UTM Appliance -Disable 21
QUESTION 12
A security engineer is troubleshooting an issue in which an employee is getting an IP address in the range on the wired
network. The engineer plus another PC into the same port, and that PC gets an IP address in the correct range. The
engineer then puts the employee\\’ PC on the wireless network and finds the PC still does not get an IP address in the proper range.
The PC is up to date on all software and antivirus definitions, and the IP address is not an APIPA address. Which of the following is MOST likely the problem?
A. The company is using 802.1x for VLAN assignment, and the user or computer is in the wrong group.
B. The DHCP server has a reservation for the PC\\’s MAC address for the wired interface.
C. The WiFi network is using WPA2 Enterprise, and the computer certificate has the wrong IP address in the SAN field.
D. The DHCP server is unavailable, so no IP address is being sent back to the PC.
Correct Answer: A
QUESTION 13
Ann, a user\\’ brings her laptop to an analyst after noticing it has been operating very slowly. The security analyst
examines the laptop and obtains the following output.
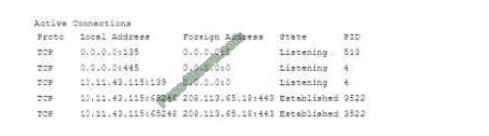
Which of the following will the analyst most likely use NEXT?
A. Process explorer
B. Vulnerability scanner
C. Antivirus
D. Network enumerator
Correct Answer: B
Click here for more questions and answers.
Free CAS-004 Dumps Q&A Download: https://drive.google.com/file/d/1qpODp9H0gl4Zn8RJWiHIJtWOpXi0D4lE/view?usp=sharing


