
Hello everyone!
Today, I’m sharing the latest CompTIA SecurityX CAS-005 dumps!
What are truly effective CompTIA SecurityX CAS-005 dumps?
- Exam materials verified through actual testing
- Instant updates to ensure real-time validity
- Aligned with real-world scenario formats
- Real-time online support
- Guaranteed success with a money-back guarantee if you fail
- Endorsed by 10+ reputable platforms
Only dumps meeting these criteria are genuinely effective CompTIA SecurityX CAS-005 dumps: https://www.pass4itsure.com/cas-005.html. Plus, you can enjoy 365 days of free updates.
Try the online practice test first:
Latest CompTIA SecurityX CAS-005 dumps practice questions
| Related | Tip | PDF Download |
| CompTIA | It is better to practice the latest than to practice a bunch of old ones | CAS-005 PDF |
Question 1:
A security analyst is conducting an investigation regarding a potential insider threat. An unauthorized USB device might have been used to exfiltrate proprietary data from a Linux system.
Which of the following options would identify the IoCs and provide the appropriate response?
A. Review the network logs and update the firewall rules.
B. Review the operating system logs and update the DLP rules.
C. Review the vulnerability logs and update the IDS rules.
D. Obtain the device ID using dmesg and update the portable storage inventory.
Correct Answer: B
Data visibility and endpoint DLP can secure data at-rest and ensure that users do not exfiltrate data via a removable device, such as a USB. The exercise does not specify if the DLP is a network or endpoint based.
Question 2:
SIMULATION
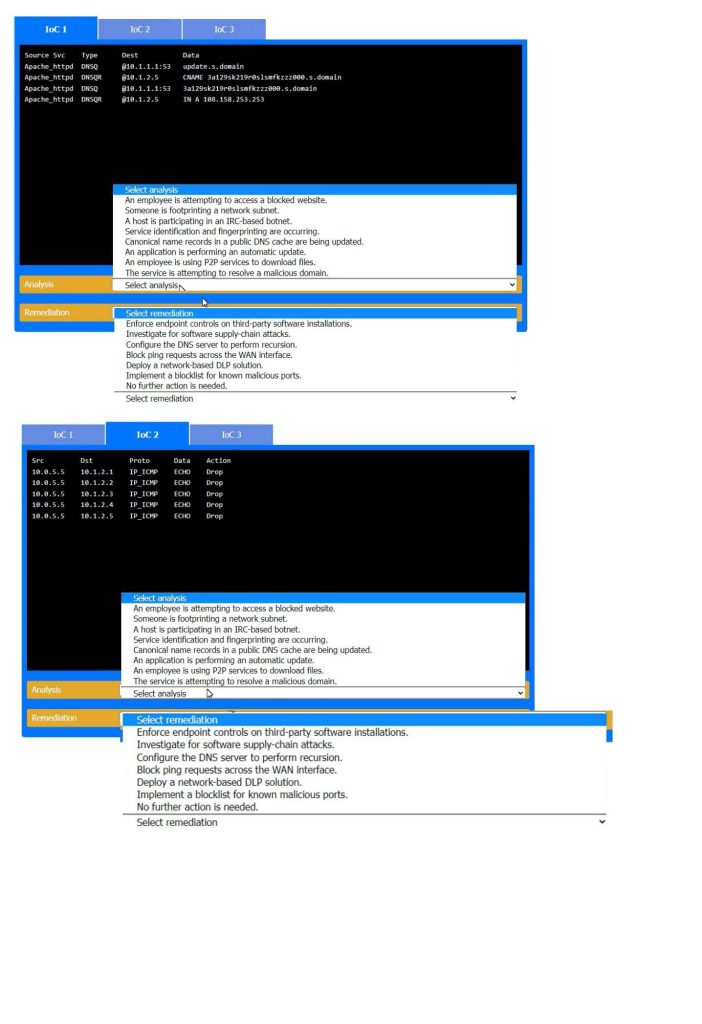
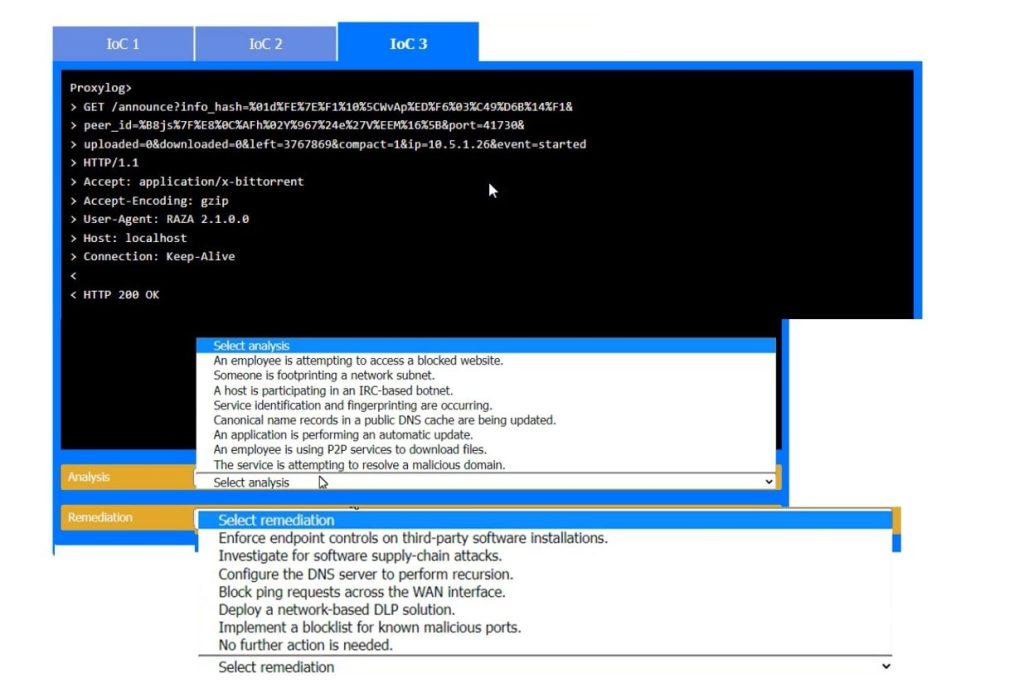
During the course of normal SOC operations, three anomalous events occurred and were flagged as potential IoCs. Evidence for each of these potential IoCs is provided.
INSTRUCTIONS
Review each of the events and select the appropriate analysis and remediation options for each IoC.
A. See the complete solution below in Explanation.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
Correct Answer: A
Analysis and Remediation Options for Each IoC:
IoC 1:
Evidence:
Analysis:
Remediation:
IoC 2:
Evidence:
Analysis:
Remediation:
IoC 3:
Evidence:
Analysis:
Remediation:
References:
CompTIA Security+ Study Guide: This guide offers detailed explanations on identifying and mitigating various types of Indicators of Compromise (IoCs) and the corresponding analysis and remediation strategies. CompTIA Security+ Exam
Objectives: These objectives cover key concepts in network security monitoring and incident response, providing guidelines on how to handle different types of security events.
Security Operations Center (SOC) Best Practices: This resource outlines effective strategies for analyzing and responding to anomalous events within a SOC, including the use of blocklists, endpoint controls, and network configuration
changes.
By accurately analyzing the nature of each IoC and applying the appropriate remediation measures, the organization can effectively mitigate potential security threats and maintain a robust security posture.
Question 3:
A vulnerability can on a web server identified the following:
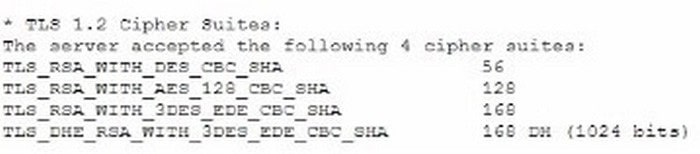
Which of the following actions would most likely eliminate on path decryption attacks? (Select two).
A. Disallowing cipher suites that use ephemeral modes of operation for key agreement
B. Removing support for CBC-based key exchange and signing algorithms
C. Adding TLS_ECDHE_ECDSA_WITH_AE3_256_GCMS_HA256
D. Implementing HIPS rules to identify and block BEAST attack attempts
E. Restricting cipher suites to only allow TLS_RSA_WITH_AES_128_CBC_SHA
F. Increasing the key length to 256 for TLS_RSA_WITH_AES_128_CBC_SHA
Correct Answer: BC
On-path decryption attacks, such as BEAST (Browser Exploit Against SSL/TLS) and other related vulnerabilities, often exploit weaknesses in the implementation of CBC (Cipher Block Chaining) mode. To mitigate these attacks, the following actions are recommended:
B. Removing support for CBC-based key exchange and signing algorithms: CBC mode is vulnerable to certain attacks like BEAST. By removing support for CBC- based ciphers, you can eliminate one of the primary vectors for these attacks. Instead, use modern cipher modes like GCM (Galois/Counter Mode) which offer better security properties.
C. Adding TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA256: This cipher suite uses Elliptic Curve Diffie-Hellman Ephemeral (ECDHE) for key exchange, which provides perfect forward secrecy. It also uses AES in GCM mode, which is not susceptible to the same attacks as CBC. SHA-256 is a strong hash function that ensures data integrity. References: CompTIA Security+ Study Guide NIST SP 800-52 Rev. 2, “Guidelines for the Selection, Configuration, and Use of Transport Layer Security (TLS) Implementations” OWASP (Open Web Application Security Project) guidelines on cryptography and secure communication
Question 4:
Recently, two large engineering companies in the same line of business decided to approach cyberthreats in a united way. Which of the following best describes this unified approach?
A. NDA
B. ISA
C. SLA
D. MOU
Correct Answer: D
Given the scenario of two large engineering companies joining forces to address cyberthreats in a united way, the most fitting description of their approach is a Memorandum of Understanding (MOU). This document formalizes their agreement to cooperate on cybersecurity matters, outlining their shared objectives, responsibilities, and possibly the methods they will use to collaborate effectively in combating cyber threats.
Question 5:
A company\’s help desk is experiencing a large number of calls from the finance department slating access issues to www bank com The security operations center reviewed the following security logs:
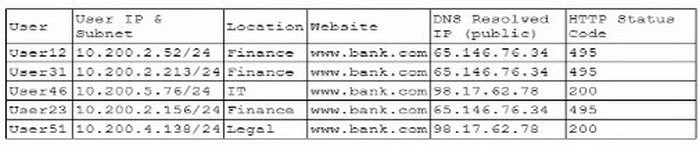
Which of the following is most likely the cause of the issue?
A. Recursive DNS resolution is failing
B. The DNS record has been poisoned.
C. DNS traffic is being sinkholed.
D. The DNS was set up incorrectly.
Correct Answer: C
Sinkholing, or DNS sinkholing, is a method used to redirect malicious traffic to a safe destination. This technique is often employed by security teams to prevent access to malicious domains by substituting a benign destination IP address.
In the given logs, users from the finance department are accessing www.bank.com and receiving HTTP status code 495. This status code is typically indicative of a client certificate error, which can occur if the DNS traffic is being manipulated or redirected incorrectly.
The consistency in receiving the same HTTP status code across different users suggests a systematic issue rather than an isolated incident. Recursive DNS resolution failure (A) would generally lead to inability to resolve DNS at all, not to a specific HTTP error.
DNS poisoning (B) could result in users being directed to malicious sites, but again, would likely result in a different set of errors or unusual activity. Incorrect DNS setup (D) would likely cause broader resolution issues rather than targeted errors like the one seen here.
By reviewing the provided data, it is evident that the DNS traffic for www.bank.com is being rerouted improperly, resulting in consistent HTTP 495 errors for the finance department users. Hence, the most likely cause is that the DNS traffic is being sinkholed.
References:
CompTIA SecurityX study materials on DNS security mechanisms. Standard HTTP status codes and their implications.
Question 6:
A software development company needs to mitigate third-party risks to its software supply chain. Which of the following techniques should the company use in the development environment to best meet this objective?
A. Performing software composition analysis
B. Requiring multifactor authentication
C. Establishing coding standards and monitoring for compliance
D. Implementing a robust unit and regression-testing scheme
Correct Answer: A
Question 7:
To bring digital evidence in a court of law, the evidence must be:
A. material.
B. tangible.
C. consistent.
D. conserved.
Correct Answer: A
For evidence to be admissible in court, it must be material, meaning it must be relevant and have a significant impact on the case. Material evidence directly relates to the facts in dispute and can affect the outcome of the case by proving or disproving a key point.
Question 8:
A company has identified a number of vulnerable, end-of-support systems with limited defensive capabilities. Which of the following would be the first step in reducing the attack surface in this environment?
A. Utilizing hardening recommendations
B. Deploying IPS/IDS throughout the environment
C. Installing and updating antivirus
D. Installing all available patches
Correct Answer: A
Question 9:
Emails that the marketing department is sending to customers are pomp to the customers\’ spam folders. The security team is investigating the issue and discovers that the certificates used by the email server were reissued, but DNS records had not been updated.
Which of the following should the security team update in order to fix this issue? (Select three.)
A. DMARC
B. SPF
C. DKIM
D. DNSSEC
E. SASC
F. SAN
G. SOA
H. MX
Correct Answer: ABC
To prevent emails from being marked as spam, several DNS records related to email authentication need to be properly configured and updated when there are changes to the email server\’s certificates:
A. DMARC (Domain-based Message Authentication, Reporting and Conformance):
DMARC records help email servers determine how to handle messages that fail SPF or DKIM checks, improving email deliverability and reducing the likelihood of emails being marked as spam. B. SPF (Sender Policy Framework): SPF
records specify which mail servers are authorized to send email on behalf of your domain. Updating the SPF record ensures that the new email server is recognized as an authorized sender. C. DKIM (DomainKeys Identified Mail): DKIM adds
a digital signature to email headers, allowing the receiving server to verify that the email has not been tampered with and is from an authorized sender. Updating DKIM records ensures that emails are properly signed and authenticated. D.
DNSSEC (Domain Name System Security Extensions): DNSSEC adds security to DNS by enabling DNS responses to be verified. While important for DNS security, it does not directly address the issue of emails being marked as spam. E.
SASC: This is not a relevant standard for this scenario. F. SAN (Subject Alternative Name): SAN is used in SSL/TLS certificates for securing multiple domain names, not for email delivery issues. G. SOA (Start of Authority): SOA records are used for DNS zone administration and do not directly impact email deliverability.
H. MX (Mail Exchange): MX records specify the mail servers responsible for receiving email on behalf of a domain. While important, the primary issue here is the authentication of outgoing emails, which is handled by SPF, DKIM, and DMARC.
References:
CompTIA Security+ Study Guide
RFC 7208 (SPF), RFC 6376 (DKIM), and RFC 7489 (DMARC) NIST SP 800-45, “Guidelines on Electronic Mail Security”
Question 10:
A security officer at an organization that makes and sells digital artwork must ensure the integrity of the artwork can be maintained. Which of the following are the best ways for the security officer to accomplish this task? (Choose two.)
A. Hashing
B. ECC
C. IPSec
D. Tokenization
E. Watermarking
F. Print blocking
Correct Answer: AE
Implementing hashing and watermarking provides a comprehensive approach to maintaining the integrity of digital artwork. Hashing allows for verification of file integrity through checksums, while watermarking embeds ownership and authenticity information directly into the artwork, deterring unauthorized use and providing proof of ownership.
Together, these measures help protect the organization\’s digital assets and ensure that customers receive genuine and unaltered digital artwork.
Question 11:
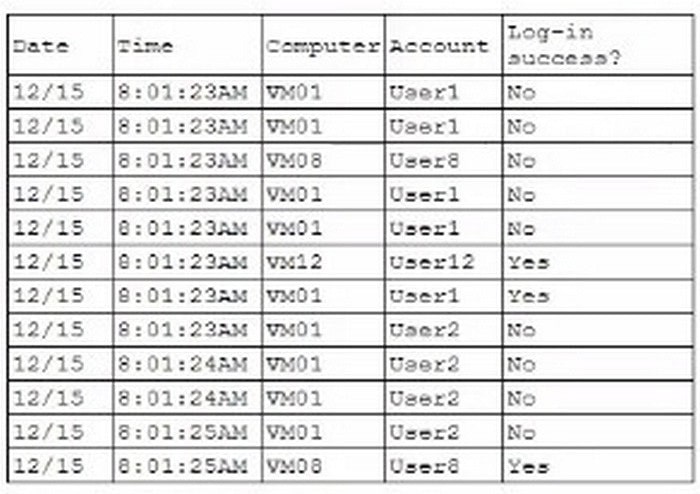
A security analyst is reviewing the following authentication logs: Which of the following should the analyst do first?
A. Disable User2\’s account
B. Disable User12\’s account
C. Disable User8\’s account
D. Disable User1\’s account
Correct Answer: D
Based on the provided authentication logs, we observe that User1\’s account experienced multiple failed login attempts within a very short time span (at 8:01:23 AM on 12/15).
This pattern indicates a potential brute-force attack or an attempt to gain unauthorized access. Here\’s a breakdown of why disabling User1\’s account is the appropriate first step:
Failed Login Attempts: The logs show that User1 had four consecutive failed login attempts:
Security Protocols and Best Practices: According to CompTIA Security+ guidelines, multiple failed login attempts within a short timeframe should trigger an immediate response to prevent further potential unauthorized access attempts. This typically involves temporarily disabling the account to stop ongoing brute- force attacks.
Account Lockout Policy: Implementing an account lockout policy is a standard practice to thwart brute-force attacks. Disabling User1\’s account will align with these best practices and prevent further failed attempts, which might lead to successful unauthorized access if not addressed.
References:
By addressing User1\’s account first, we effectively mitigate the immediate threat of a brute- force attack, ensuring that further investigation can be conducted without the risk of unauthorized access continuing during the investigation period.
Question 12:
Users are willing passwords on paper because of the number of passwords needed in an environment.
Which of the following solutions is the best way to manage this situation and decrease risks?
A. Increasing password complexity to require 31 least 16 characters
B. implementing an SSO solution and integrating with applications
C. Requiring users to use an open-source password manager
D. Implementing an MFA solution to avoid reliance only on passwords
Correct Answer: B
Implementing a Single Sign-On (SSO) solution and integrating it with applications is the best way to manage the situation and decrease risks. Here\’s why:
Reduced Password Fatigue: SSO allows users to log in once and gain access to multiple applications and systems without needing to remember and manage multiple passwords. This reduces the likelihood of users writing down passwords.
Improved Security: By reducing the number of passwords users need to manage, SSO decreases the attack surface and potential for password-related security breaches. It also allows for the implementation of stronger authentication methods.
User Convenience: SSO improves the user experience by simplifying the login process, which can lead to higher productivity and satisfaction.
References:
Question 13:
A security architect examines a section of code and discovers the following:
1.
char username[20]
2.
char password[20]
3.
gets(username)
4.
checkUserExists(username)
Which of the following changes should the security architect require before approving the code for release?
A. Allow only alphanumeric characters for the username.
B. Make the password variable longer to support more secure passwords.
C. Prevent more than 20 characters from being entered.
D. Add a password parameter to the checkUserExists function.
Correct Answer: C
The code snippet provided is vulnerable to a buffer overflow attack due to the use of the gets function, which does not limit the input size.
This can lead to memory corruption and potential security vulnerabilities. By ensuring that no more than 20 characters are entered, the code can prevent buffer overflow attacks, thus mitigating a significant security risk.
Question 14:
A company\’s security policy states that any publicly available server must be patched within 12 hours after a patch is released A recent llS zero-day vulnerability was discovered that affects all versions of the Windows Server OS:
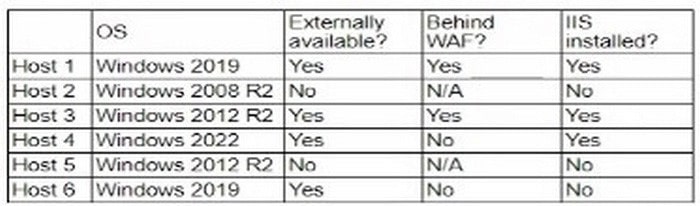
Which of the following hosts should a security analyst patch first once a patch is available?
A. 1
B. 2
C. 3
D. 4
E. 5
F. 6
Correct Answer: A
Based on the security policy that any publicly available server must be patched within 12 hours after a patch is released, the security analyst should patch Host 1 first. Here\’s why:
Public Availability: Host 1 is externally available, making it accessible from the internet. Publicly available servers are at higher risk of being targeted by attackers, especially when a zero-day vulnerability is known. Exposure to Threats:
Host 1 has IIS installed and is publicly accessible, increasing its exposure to potential exploitation. Patching this host first reduces the risk of a successful attack.
Prioritization of Critical Assets: According to best practices, assets that are exposed to higher risks should be prioritized for patching to mitigate potential threats promptly.
Question 15:
A security engineer is given the following requirements:
1.
An endpoint must only execute Internally signed applications
2.
Administrator accounts cannot install unauthorized software.
3.
Attempts to run unauthorized software must be logged
Which of the following best meets these requirements?
A. Maintaining appropriate account access through directory management and controls
B. Implementing a CSPM platform to monitor updates being pushed to applications
C. Deploying an EDR solution to monitor and respond to software installation attempts
D. Configuring application control with blocked hashes and enterprise-trusted root certificates
Correct Answer: D
To meet the requirements of only allowing internally signed applications, preventing unauthorized software installations, and logging attempts to run unauthorized software, configuring application control with blocked hashes and enterprise-trusted root certificates is the best solution.
This approach ensures that only applications signed by trusted certificates are allowed to execute, while all other attempts are blocked and logged. It effectively prevents unauthorized software installations by restricting execution to pre-approved applications.
References:
CompTIA SecurityX Study Guide:
Describes application control mechanisms and the use of trusted certificates to enforce security policies.
NIST Special Publication 800-53, “Security and Privacy Controls for Information Systems and Organizations”: Recommends application whitelisting and execution control for securing endpoints. “The Application Security Handbook” by Mark Dowd, John McDonald, and Justin Schuh:
Covers best practices for implementing application control and managing trusted certificates
Be sure to use genuine and effective CompTIA SecurityX CAS-005 dumps. The latest version includes 290 exam questions and answers. Visit https://www.pass4itsure.com/cas-005.html and choose either PDF or VCE to help you pass the exam with ease.